9 Tips to Transition from Cybersecurity to Blockchain Security Researcher
Introduction
The Growing Importance of Blockchain Security
In an era where digital assets and decentralized systems dominate industries, blockchain security has become paramount. With billions of dollars flowing through cryptocurrencies, smart contracts, and decentralized finance (DeFi) platforms, safeguarding these systems is critical. Blockchain security ensures trust, integrity, and resilience, directly impacting the future of innovation in Web3 technologies.
Cybersecurity and Blockchain Security: A Natural Convergence
The transition from cybersecurity to blockchain security is a logical leap for professionals in the tech domain. Both fields demand a deep understanding of threats, cryptographic principles, and system vulnerabilities. However, blockchain adds new layers of complexity, including decentralized networks and immutable ledgers. For cybersecurity experts, leveraging their foundational knowledge and adapting to blockchain’s unique challenges offers a rewarding pathway into this cutting-edge field.
What to Expect: 9 Actionable Tips for a Seamless Transition
This guide outlines nine practical tips to help cybersecurity professionals successfully pivot into blockchain security research. From mastering blockchain fundamentals to building niche expertise, these steps will equip you with the knowledge and skills to thrive in a rapidly evolving landscape.
Master the Fundamentals of Blockchain Technology
Importance of Understanding Distributed Ledger Technology
Blockchain technology is built on distributed ledgers, enabling transparent and tamper-resistant records of transactions. This foundational concept underpins the entire blockchain ecosystem and differentiates it from traditional systems.
Overview of Blockchain Architecture, Types, and Security Nuances
Dive deep into blockchain architecture to understand how networks achieve consensus, validate transactions, and maintain decentralization. Explore the distinctions between public, private, and permissioned blockchains, as each type presents unique security considerations. For instance, while public blockchains like Bitcoin prioritize transparency, private blockchains might focus on controlled access and enterprise security.
Suggested Learning Resources and Key Platforms to Explore
- Ethereum: Explore smart contracts and decentralized applications.
- Bitcoin: Understand proof-of-work and the first blockchain’s foundational design.
- Educational Resources: Coursera, Udemy, and YouTube offer beginner-friendly courses on blockchain basics. Whitepapers, like Bitcoin’s original, also provide critical insights.
Learn Relevant Programming Languages
Essential Programming Skills: Solidity, Python, JavaScript
To thrive in blockchain security, proficiency in specific programming languages is non-negotiable:
- Solidity: The go-to language for writing and analyzing smart contracts on Ethereum.
- Python: Widely used for blockchain development and creating security analysis tools.
- JavaScript: Essential for building Web3 interfaces and interacting with blockchain networks.
Overview of How These Languages Are Used in Blockchain Development and Security
- Solidity enables the creation and auditing of smart contracts, critical for identifying vulnerabilities like reentrancy or overflow bugs.
- Python facilitates backend blockchain development and automated security testing tools.
- JavaScript powers user-facing applications that interact with blockchain protocols via Web3 libraries.
Recommendations for Courses and Hands-on Practice Resources
- Solidity: CryptoZombies gamifies smart contract development for beginners.
- Python: Platforms like Codecademy and Coursera offer Python courses tailored to blockchain.
- JavaScript: FreeCodeCamp provides comprehensive tutorials for Web3 integration.
- Practice Tip: Use testnets (e.g., Rinkeby or Goerli) to deploy and test smart contracts without real-world risks.
Understand Cryptography and Its Applications in Blockchain
The Role of Cryptography in Blockchain Security
Cryptography is the backbone of blockchain security, ensuring data integrity, confidentiality, and authentication across decentralized networks. It empowers blockchain systems to function securely without a centralized authority, making it a cornerstone for trust and resilience in the ecosystem.
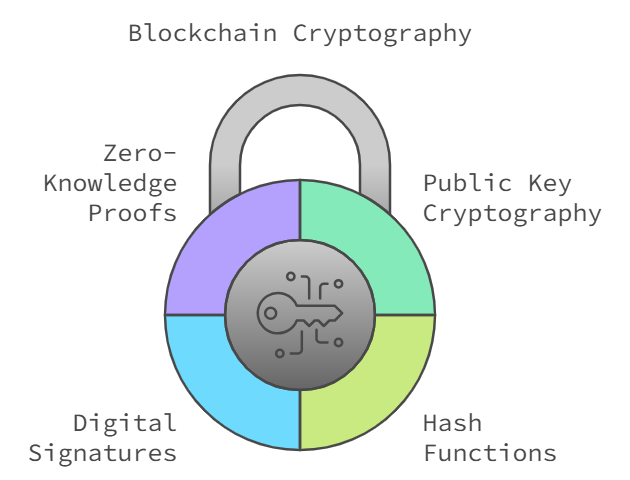
Key Concepts in Blockchain Cryptography
- Public Key Cryptography: Facilitates secure transactions and wallet interactions by using a pair of public and private keys.
- Hash Functions: Ensure data immutability and integrity by converting input data into a fixed-length string. Common examples include SHA-256 and Keccak-256.
- Digital Signatures: Authenticate transaction origins, ensuring only authorized entities can initiate actions.
- Zero-Knowledge Proofs: Allow users to verify claims without revealing underlying data, crucial for privacy-focused applications like zk-SNARKs.
Suggestions for Deepening Knowledge and Practical Applications
- Study cryptographic protocols using resources like Kahn Academy and Coursera.
- Experiment with libraries like PyCryptodome (Python) or Web3.js (JavaScript) to implement cryptographic operations.
- Explore advanced topics such as elliptic curve cryptography (ECC) and secure multiparty computation (SMPC).
Study Common Blockchain Vulnerabilities and Attack Vectors
Overview of Common Threats
- 51% Attacks: Occur when a malicious actor gains majority control of a blockchain network, enabling them to double-spend or disrupt operations.
- Smart Contract Vulnerabilities: Bugs like reentrancy attacks or integer overflows can lead to significant financial losses.
- Sybil Attacks: Malicious entities create multiple identities to gain disproportionate influence on a network.
- Eclipse Attacks: Isolate a node from the network to manipulate its view of the blockchain.
Case Studies of Past Incidents and Lessons Learned
- The DAO Hack (2016): Exploited a reentrancy vulnerability in a smart contract, resulting in $60 million stolen. Lesson: Thoroughly audit smart contracts before deployment.
- Bitcoin Gold 51% Attack (2018): Highlighted the risks of insufficient network decentralization. Lesson: Encourage diverse and distributed node participation.
Resources for Staying Informed About New Vulnerabilities
- Follow platforms like CoinDesk and The Block for news.
- Participate in forums like Ethereum's Reddit or specialized Discord groups.
- Read technical reports and postmortems from blockchain security firms such as Trail of Bits or CertiK.
Gain Hands-on Experience with Security Tools
Overview of Static and Dynamic Analysis Tools
- Static Analysis Tools: Analyze code for vulnerabilities without executing it. Examples include Slither and MythX.
- Dynamic Analysis Tools: Test code behavior in controlled conditions. Tools like Echidna simulate various scenarios to uncover runtime vulnerabilities.
How Blockchain Explorers and Platforms Assist in Security Analysis
Blockchain explorers, such as Etherscan or Blockchair, allow researchers to track transactions, inspect smart contract code, and analyze network activity. They’re invaluable for investigating anomalies or potential exploits.
Tips for Practical Application in Controlled Environments
- Use testnets like Ropsten or Binance Testnet to experiment without financial risks.
- Set up a local blockchain environment with Ganache to simulate attacks or test contract changes.
- Regularly practice with tools by analyzing open-source blockchain projects or participating in bug bounty programs.
Participate in Capture The Flag (CTF) Competitions
Benefits of Engaging in CTF Competitions for Skill-Building
CTF competitions provide hands-on, practical learning opportunities to solve real-world security challenges. These contests enhance your problem-solving skills, deepen your understanding of blockchain vulnerabilities, and keep you up-to-date with the latest attack vectors. They’re also a great way to demonstrate your expertise to potential employers or collaborators.
Highlight on Blockchain-Specific CTF Platforms
- Paradigm CTF: Offers challenges specifically tailored to Web3 and blockchain security, focusing on areas like smart contract vulnerabilities and exploit development.
- CTFtime.org: Tracks upcoming blockchain and general cybersecurity competitions.
- Ethernaut: A game-based platform by OpenZeppelin to test smart contract hacking skills.
Tips for Preparing and Succeeding in These Challenges
- Familiarize yourself with blockchain tools like Remix, Ganache, and Etherscan.
- Study write-ups from past CTF events to understand common challenge types and solutions.
- Practice regularly on CTF platforms and participate in team-based competitions to learn collaboratively.
Contribute to Open Source Projects
Advantages of Working on Open-Source Blockchain Security Projects
Open-source contributions allow you to gain real-world experience, improve your technical skills, and build a portfolio. You’ll also collaborate with industry professionals and grow your network, paving the way for career opportunities.
Types of Projects to Consider and How to Get Involved
- Smart Contract Security Auditing Tools: Contribute to tools like Slither or Mythril.
- Blockchain Explorers: Help enhance platforms like Etherscan with security features.
- Security Protocols: Participate in developing frameworks for secure blockchain operations, such as zk-SNARK-based privacy solutions.Find projects on platforms like GitHub by searching repositories tagged with blockchain or security. Join developer communities on Discord or Telegram to discover collaborative opportunities.
Building Reputation and Networking Through Community Contributions
Active contributions position you as a thought leader in the blockchain security space. Regular commits, insightful pull requests, and engaging discussions within the community build your credibility and expose you to like-minded professionals and organizations.
Stay Updated on the Latest Developments
Importance of Keeping Up with Industry Changes
Blockchain technology evolves at breakneck speed, with new protocols, tools, and vulnerabilities emerging frequently. Staying informed helps you maintain a competitive edge and ensures that your security strategies are relevant and effective.
Sources for Staying Informed
- Social Media: Follow blockchain experts and researchers on Twitter (e.g., Vitalik Buterin, Paradigm).
- Research Papers and Technical Blogs: Stay updated through platforms like ArXiv and Medium.
- Conferences and Webinars: Attend events such as DEF CON Blockchain Village, ETHGlobal, or Consensus.
Specific Blogs, Newsletters, and Forums to Follow
- Blogs: Trail of Bits, CryptoSec.info.
- Newsletters: Cyfrin Newsletter, Paradigm Weekly.
- Forums: Ethereum and Bitcoin developer forums, specialized Discord communities.
Build a Specialization
Benefits of Focusing on Niche Areas Within Blockchain Security
Specializing helps you establish expertise in high-demand areas, setting you apart in the job market. You’ll become a go-to professional for specific security challenges, enhancing your career growth and earning potential.
Popular Specializations in Blockchain Security
- Smart Contract Auditing: Detect and mitigate vulnerabilities in decentralized applications.
- DeFi Security: Secure decentralized finance platforms against exploits and hacks.
- Cross-Chain Interoperability: Address security challenges in bridging multiple blockchain ecosystems.
- Privacy Solutions: Work on advanced cryptographic techniques like zk-SNARKs.
Steps to Identify and Develop Expertise in a Specific Area
- Research trending topics in blockchain security through industry reports and discussions.
- Take advanced courses or attend workshops tailored to your chosen specialization.
- Build practical experience by contributing to niche projects, auditing smart contracts, or writing technical articles.
- Network with professionals in your field to exchange insights and collaborate on research or solutions.
Conclusion
Recap of the Transition Journey and Its Key Components
Transitioning from cybersecurity to blockchain security is an exciting journey filled with opportunities to learn, innovate, and make an impact in a rapidly evolving field. From mastering blockchain fundamentals to building expertise in cryptography, participating in CTF competitions, and staying updated on the latest developments, each tip serves as a stepping stone toward your goal.
Encouragement for Consistent Effort and Learning
This journey requires persistence, a commitment to continuous learning, and practical application of skills. Embrace the challenges as opportunities to grow and refine your expertise. Remember, every expert in blockchain security once started as a beginner.
Don’t wait to get started. Choose one tip from this list—whether it’s exploring Ethereum basics or joining a CTF competition—and take the first step today. Momentum builds success, and your dedication will drive you to become a proficient blockchain security researcher.